Scenario-based Safety and Security Analysis
Meta-Information
Origin: Eike Möhlmann, Sebastian van der Maelen, Thomas Strathmann (all OFFIS)
Written: May 2019
Purpose: Refinement of functional requirements into safety and security requirements and corresponding abstract scenarios in which the requirements have to be satisfied.
To consider: The performed hazard and risk analysis as well as thread and risk analysis could use standards like the ISO26262, ISO/WD PAS 21448, SEA J 3061 and consider abstract scenarios.
Structure
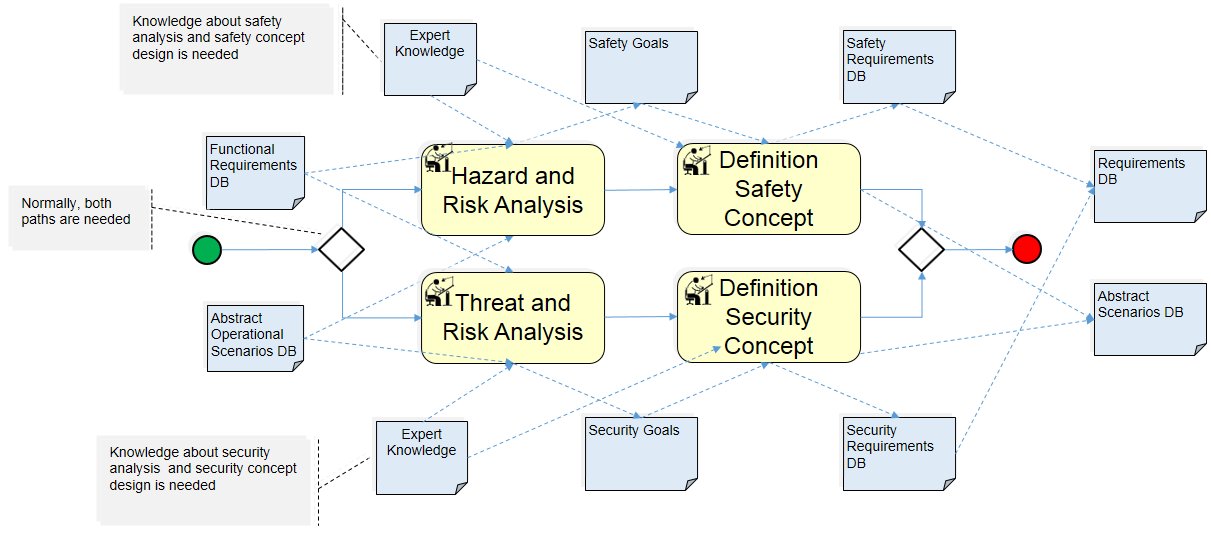
Participants and Important Artefacts
Functional Requirements DB: A set of functional requirements for the SUT.
Abstract Operational Scenarios DB: A set or catalog of abstract scenarios which have been reconstructed from real world data by observing the deployment context of the SUT.
Safety and Security Goals: A set of safety and security goals the have to be satisfied to not violate the functional requirements.
Safety and Security Requirements DB: A refined set of safety and security requirements on the system-under-test which have been derived from analyzing operational scenarios.
Abstract Scenarios DB: A set or catalog of abstract scenarios in which the requirements have to be satisfied.
Actions/Collaborations
Hazard and Risk Analysis (see e.g. ISO26262): Identification of safety hazards and their associated risk (exposure and impact) on the (high level) functional requirements to derive safety goals preventing these hazards.
Threat and Risk Analysis (see e.g. SEA J 3061): Identification of security threats and their associated risk (exposure and impact) on the (high level) functional requirements to derive security goals preventing these threats.
Definition Safety Concept: Refinement of the safety goals into (functional) safety requirements.
Definition Security Concept: Refinement of the security goals into (functional) security requirements.
Discussion
Benefits: Systematic identification of safety hazards and security threats and derivation of a (safety & security) requirement DB which will prevent the identified hazards and threats.
Application Examples
Generation of a domain specific requirements database with (semi-)virtual verification.
Relations to other Patterns
| Pattern Name | Relation* |
| Requirement and Scenario Elicitation | This pattern elaborates the requirements for that pattern (which is the super-pattern of this pattern) |
* “this pattern” denotes the pattern described here, “that pattern” denotes the related pattern
