Security Risk Assessment with Attack Trees
Meta-Information
Origin: Stefan Jakšić, Wolfgang Herzner, Verma Siddhartha (all AIT).
This pattern has been developed within the project IoT4CPS.
Written: June 2020
Purpose: Assess potential security risks for a (to be developed) CPS using attack trees.
To consider: For basic threats, it should be known how likely they are, as well as how hazardous higher level threats can be.
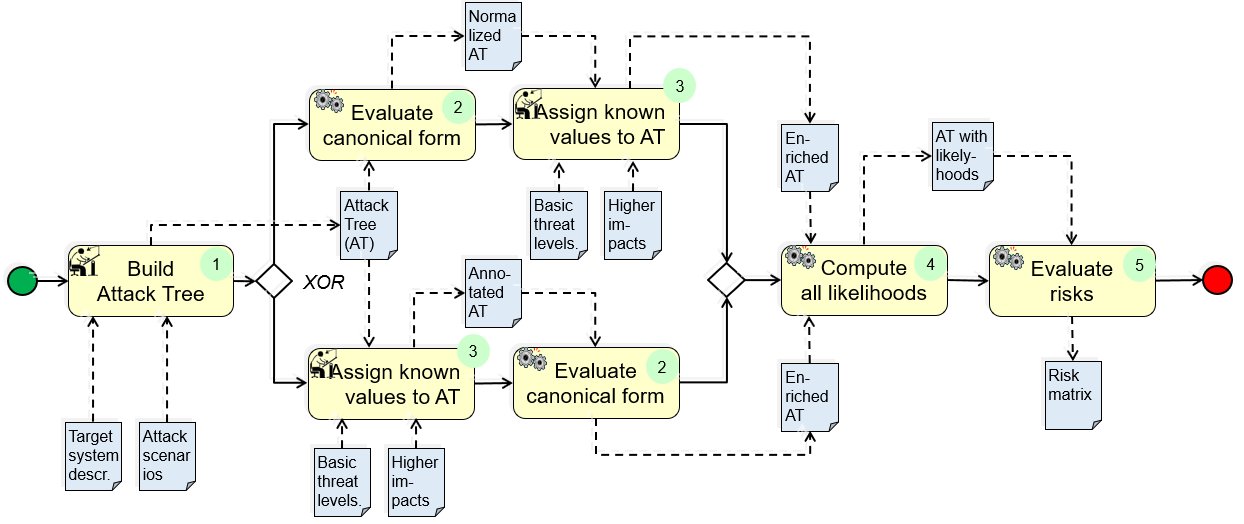
Structure
Definitions
Attack Tree (AT): A tree graph with inner nodes representing logical OR/AND/SAND operations of lower level tree elements.
Basic Attack (BA): Bottommost AT nodes, representing atomic or elementary security threats.
Higher Attack State (HAS): All not BA-nodes in the AT.
Impact (Strength) / Severity Level: Severity of consequences of a successful attack.
Likelihood / Threat Level: Probability of occurance of a certain threat or attack.
Risk: Impact * Likelihood.
Target System (TS): The CPS for which security risks shall be analyzed.
.
Participants and Important Artefacts
System Expert: Person that has sufficient knowledge about the TS for providing all relevant information to the →
Security Expert: Person who can identify all BAs relevant for the TS, and who knows how they interrelate in order to build the AT.
Target System Description: Information at sufficient detail about the TS that can be used by the experts for building the appropriate AT.
Attack Scenarios: Considering known attack scenarios help avoiding omission of relevant security threats.
Attack Tree: Tree-like graph representing deriviation of complex threats from basic attacks.
Basic Threat Levels: Likelihoods of BAs.
Higher Impacts: Impacts of higher nodes in the BA tree (that are known a priori).
Normalized AT: AT turned into disjunctive normal form (DNF).
Enriched AT: Normalized AT, annotated with basic threat levels and higher impacts.
AT with Likelihoods: Enriched AT with likelihoods computed for all nodes.
Risk Matrix: Matrix showing the risks of all attacks for all target system. components/items.
.
Actions and Collaborations
(1) Build Attack Tree:
(1.a) Identify the BA that are principally possible for the given TS.
(1.b) Multiple attack scenarios are considered by combining BAs via ‘OR‘, ‘AND’, and ‘SAND’ (sequential AND) nodes, reflecting experts knowledge about their combinatorial characteristics.
(1.c) Multi-stage attacks are considered by iterating step 2, including new nodes, in a tree-like manner until a topmost attack threat is reached.
(2) Evaluate canonical form: For considering OR combination of attacks, evaluate the canonical form (DNF – Disjunctive Normal Form) of the attack tree. In canonical form all the attack paths are related to an attack state with OR (disjunction) relations. Now, each attack path consists of several basic attack steps related with (S)AND ((sequential) conjunction). This means the attack path will be successful if and only if all the basic attack steps involved are successful.
(3) Assign known values to AT: Assign ordinal (e.g. “very low” ≈ 0 … “very high” ≈ 3) threat levels to BAs’, and quantitative severity levels to all higher nodes of the AT.
(4) Compute all likelihoods: For the higher level and multi-level attacks represented (HAS) by the non-leave nodes of the AT, their likelihoods are computed as follows:
(4.a) For OR nodes, the canonical form gives all attack paths to each state related with OR (disjunction) and we do the risk assessment for each attack paths individually. Note that the resulting risks are propagated separately to the next higher level.
(4.b) For AND nodes, likelihood is the minimum of all direct lover level nodes.
(4.c) For SAND nodes, compute likelihood as for AND nodes (i.e. do not consider the impact of sequential dependences on threat level). (The reachability score for following attacks can be taken as preceding attack, as this provides a gateway to the following attacks.)
(5) Evaluate risks (risk matrix): For each node, compute risk as product likelihood*impact. Represent the result in a matrix with all TS components on one axis, and all threats – basic as well as higher and multi – on the other.
.
Discussion
Note on process flow: In principle, activities 2 and 3 can be executed in revers order. This is reflected in the structure diagram.
Benefits: Compared to other TARA-approaches (Threat Analysis and Risk Assessment), this approach enables consideration of multiple and multi-stage attacks in both qualitative or quantitative fashion.
Limitation: Without knowing likelihoods of BA and impacts of included multiple and multi-stage attacks, computing all attack risks is not possible.
.
Application Example
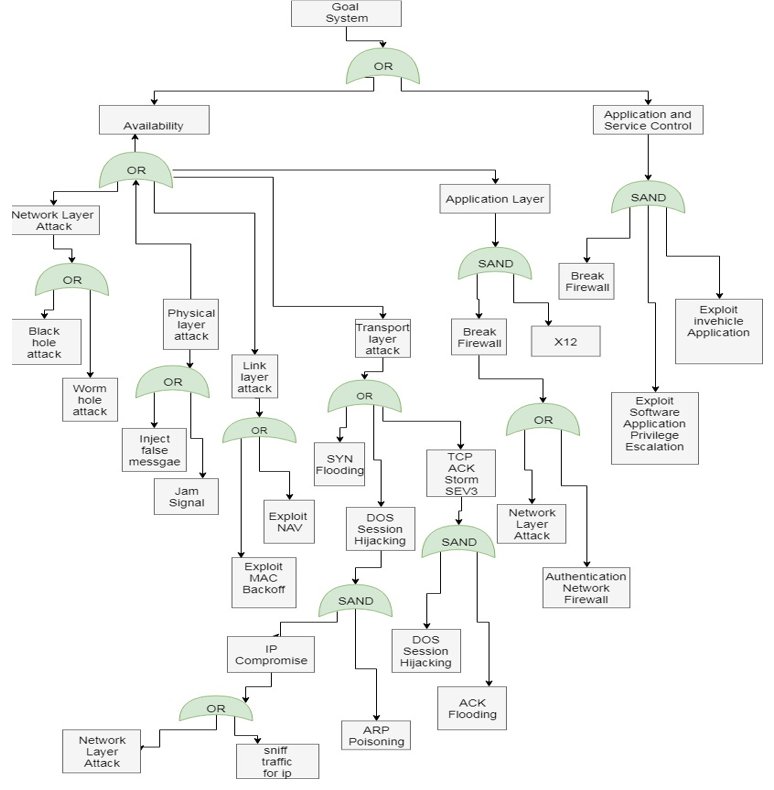
This example shows the application to the threats listed in “Review of safety mechanism in vehicular ad-hoc networks” (Alexandria Engineering Journal (2015) 54, 1115–1126).
(1) The first version of the Attack Tree at right is drawn using www.draw.io (see figure below).
(2) For risk assessment, it is drawn with ADTool, see 2nd figure below.
(3) Then, Basic VBA scripts evaluate, for all higher attacks, which are the basic attack steps involved and how they are related using ‘AND’, ‘OR’, ‘SAND’ (3rd figure below).
(4) These scripts then evaluate the disjunctive normal form.
(5) Finally, for each attack path, the critical basic attack and its likelihood is evaluated, and the obtained risks shown in the risk matrix (last figure).
.
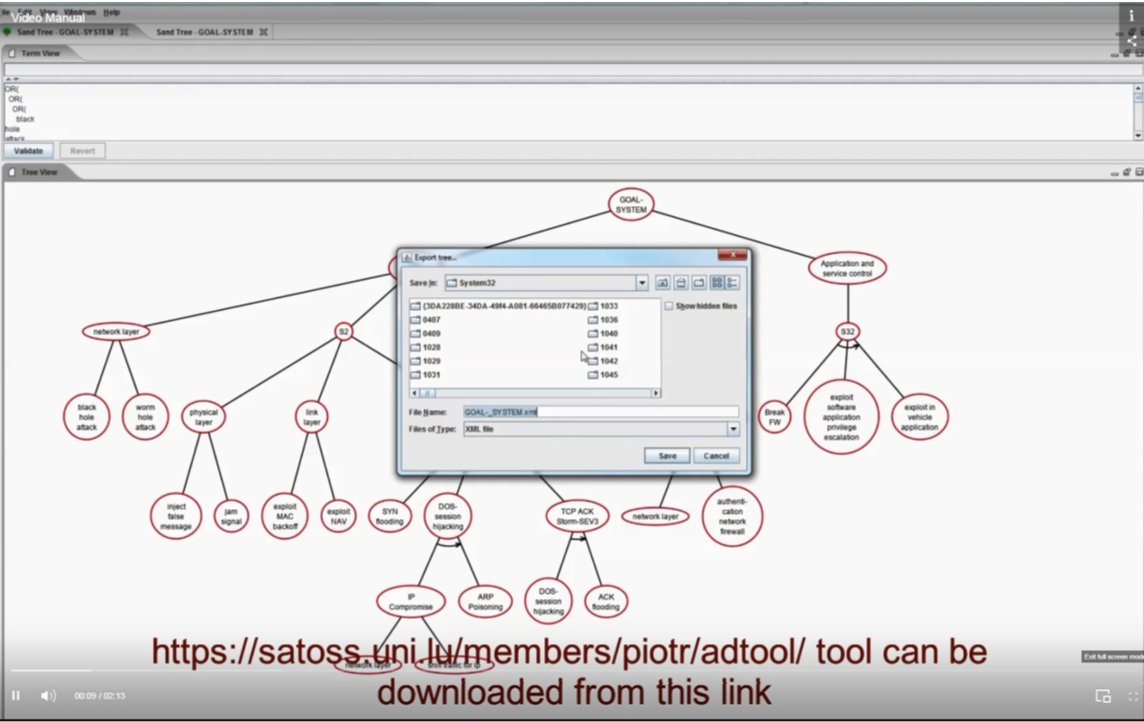
The AT obtained using ADTool
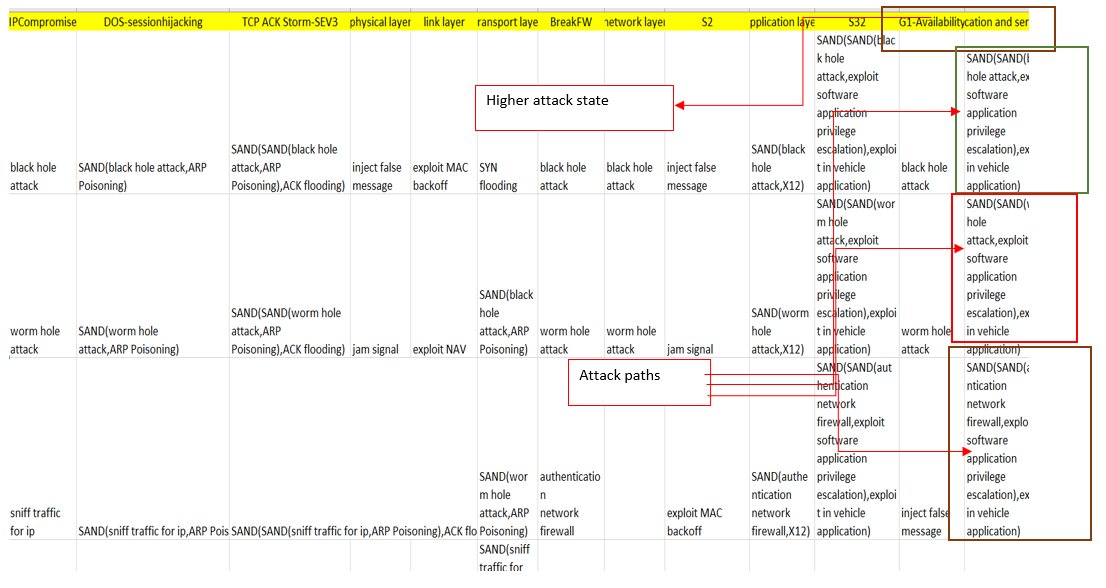
E.g. the higher attack G1 consists of 3 attack paths
.
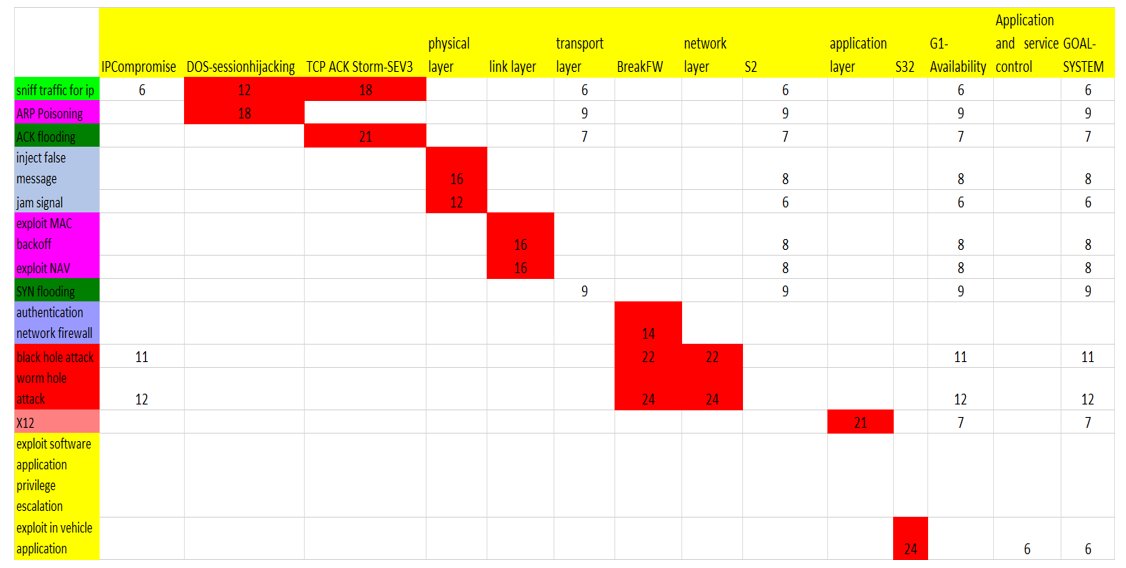
Risk matrix with critical basic attacks
.
Relations to other Patterns
| Pattern Name | Relation* |
| Derive Safety Requirements (for Automated Driving) | That pattern uses similar tree-based analysis techniques (fault tree, HARA) |
| Physical Wireless Security | That pattern can use this pattern in its step 2 |
| Scenario-based Safety and Security Analysis | That pattern can use this pattern alternatively in its “Threat and Risk Analysis” |
* “this pattern” denotes the pattern described here, “that pattern” denotes the related pattern
