Physical Wireless Security
Meta-Information
Origin: Lukasz Szczygielski, Michal Tarkowski, Przemyslaw Popowicz / all GUT
Written: April 2019
Purpose: Verification of physical wireless secure communication between different nodes. The secure communication is interpreted as a jamming resistant. The pattern can be used to define test strategy in different domain.
Context/Pre-Conditions:
– The basic information about wireless communication channel must be known.
– General information about the scene (physical location of system deployemnt place) must be known.
To consider: The pattern is focused on physical aspects of wireless communication in the ACPS. The pattern does not specify specific countermeasures, KPI’s or techniques.
Structure
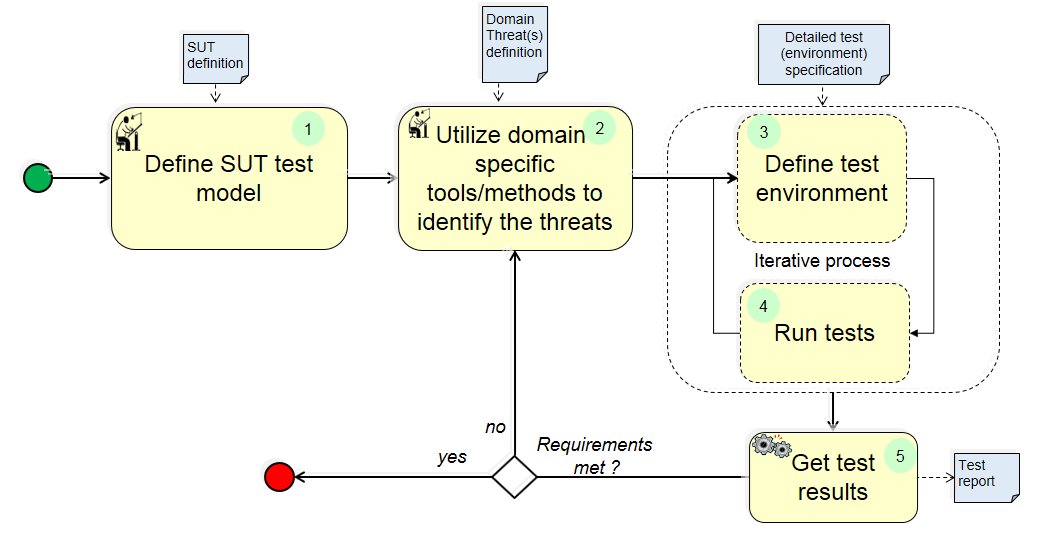
xxxxxxxxxxxxxxxDefine test environmentxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxRun tests
Participants and Important Artefacts
Test engineer: person responsible for planning the test, interpreting the results and outcomes as well as defining basic test parameters (communication channel model, threat type etc.).
SUT Definition: concise definition of system that for which security of its wireless comm. shall be shown.
Domain Threat(s) definition: Each domain may Focus on different type of threats – jamming, man-in-the-middle etc.. In order to define proper test process, domain threats must be identified.
Detailed Test (Environment) specification: Test specification contains basic information about the wireless communication security tests – Threat type, number of test iteration, environment model, countermeasures, communication channel etc.
Test Report: Test results present test outcomes in predefined structure – e.g. jamming resistance score, evaluation of overall security level.
Actions and collaborations
(1) Define test model: SUT model is defined, precise test objectives are defined, test objects (a part of wireless communication system) are identified.
(2) Define threats: In order to identify key threats type in domain specific environments, different techniques and methods apply.
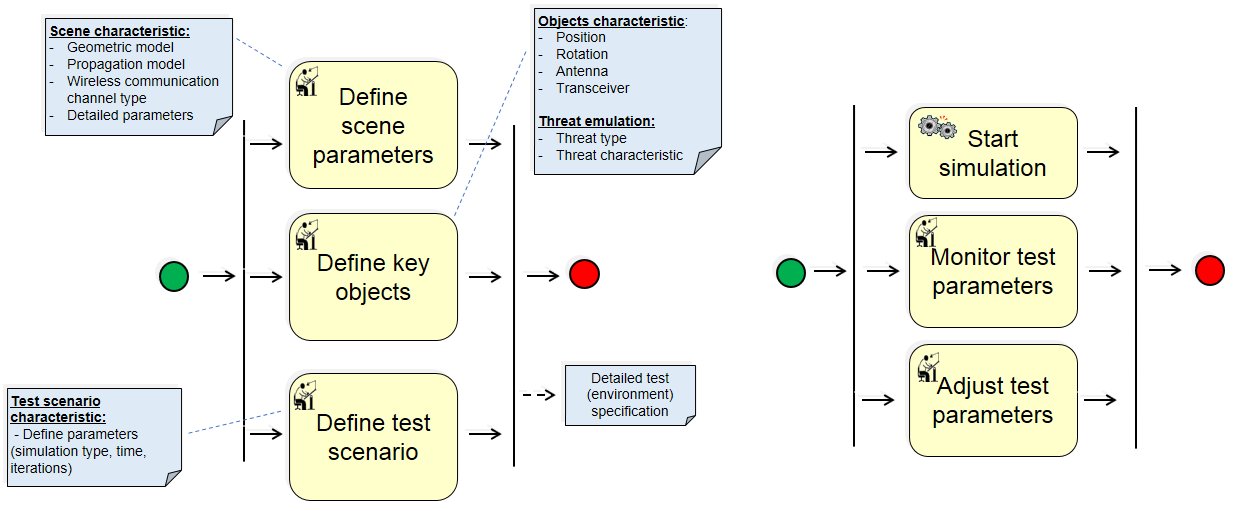
(3) Define test environment: Definition of test environment covers reflecting real world condition into simulation environment.
(4) Run tests: Predefined tests are executed on test platform. Steps 3 and 4 are iterated until tests are sufficiently unambiguous.
(5) Get test results: Test results are based on predefined sets of metrics, charts and any other suitable form of related data presentation.
Discussion
– The presented concept is a framework based on PhyWiSe tool, developed by GUT. To some extent, this tool is inherent part of the pattern.
– Each step of the whole process requires some additional work. Amount of this work depends on domain / use case / individual requirements
– Definition of SUT model requires basic knowledge about utilized communication standards, devices
Application Examples
The pattern is utilized to evaluate physical wireless communication security in different domains.
A core component in all application examples is the „PhyWise“ tool: a dedicated software environment that allows for time-sensitive testing of wireless communication security.
Relations to other Patterns
| Pattern Name | Relation |
| Scenario-based Safety & Security Analysis | Can be used to identify threats (activity 2) |
| Security Risk Assessment with Attack Trees | Can be used to identify threats (activity 2) |
