IC Security Certification
Meta-Information
Origin: Kiran Shekhar / NXPGE
Written: April 2019
Purpose: For design and manufacture of integrated circuit/chip whose security features & functionality can be evaluated & certified/qualified by independent international standardization authorities.
Context/Pre-Conditions: Security Target/Protection profile defined.
To consider: Requires expertise on IC Hardware Analog & Digital design. For certification process, expertise on Target of evaluation description, Threats, Assumptions, Security objectives, Security functional requirements, Security Assurance requirements & Rationales.
Structure
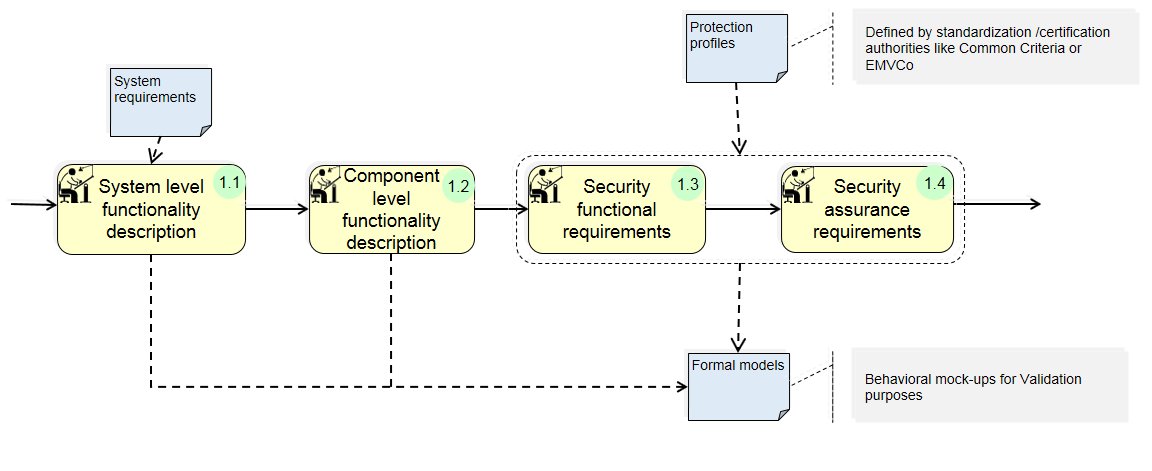
(1) System Specifications:
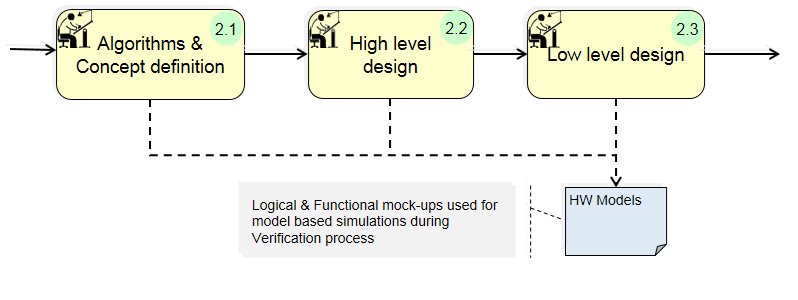
(2) Architecture/Design:
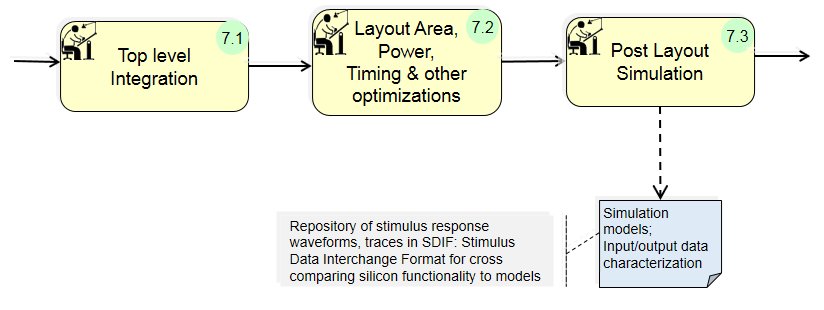
(7) Place & Route:
(8) Pre-silicon Security Analysis / Evaluation:
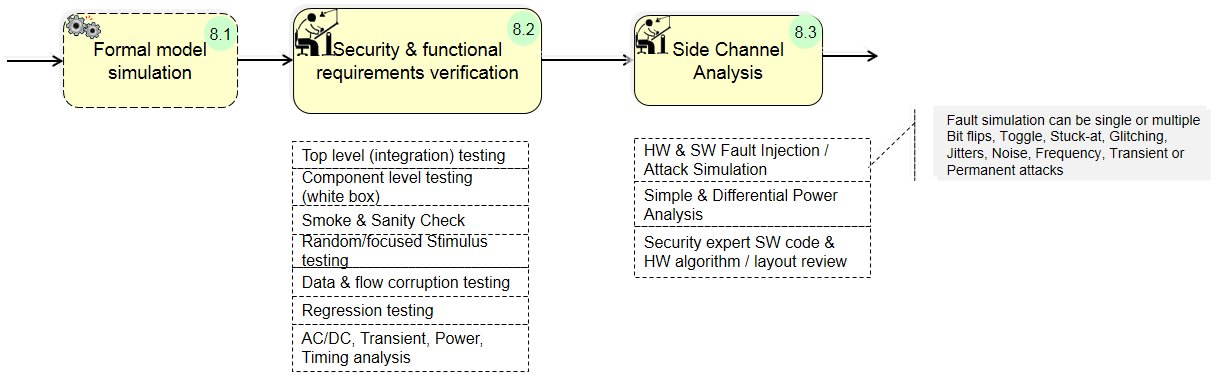
(8.1) Formal Model Simulations:
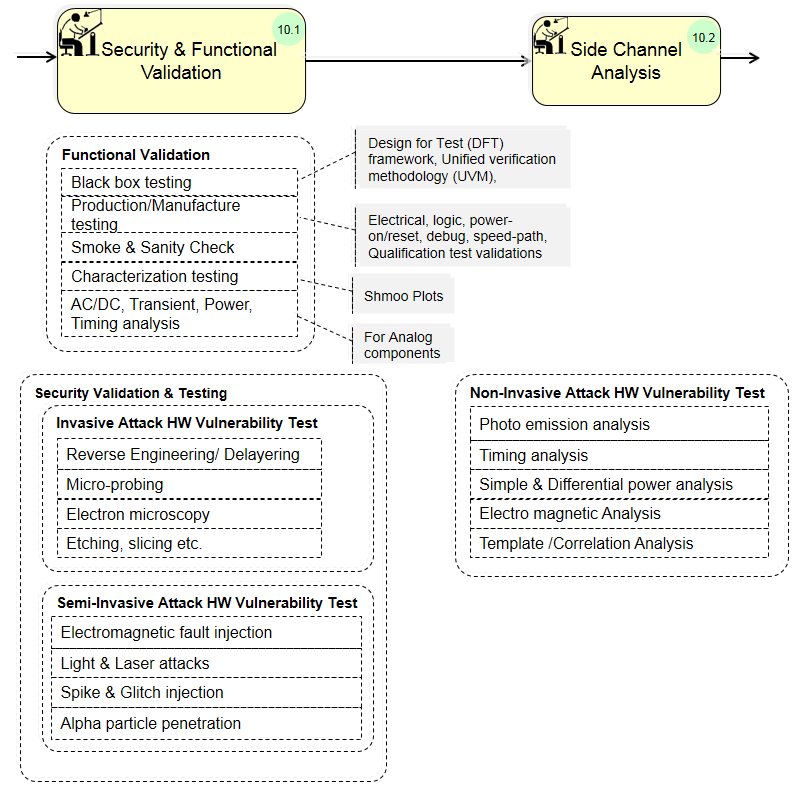
(10) Post-silicon Security Analysis/ Evaluation:
Participants and Important Artefacts
Participants:
Cryptographer: Brings knowledge about security protocols, algorithm.
IP Designer: Experts who implement the security IC which include Architects, Hardware, Software engineers.
V&V Engineer: Pre-silicon & Post-silicon verification & validation experts who ensure security functionality are correctly implemented.
Security Analyst: Has background of security threats, attack vectors, certification & standards requirements.
Artefacts:
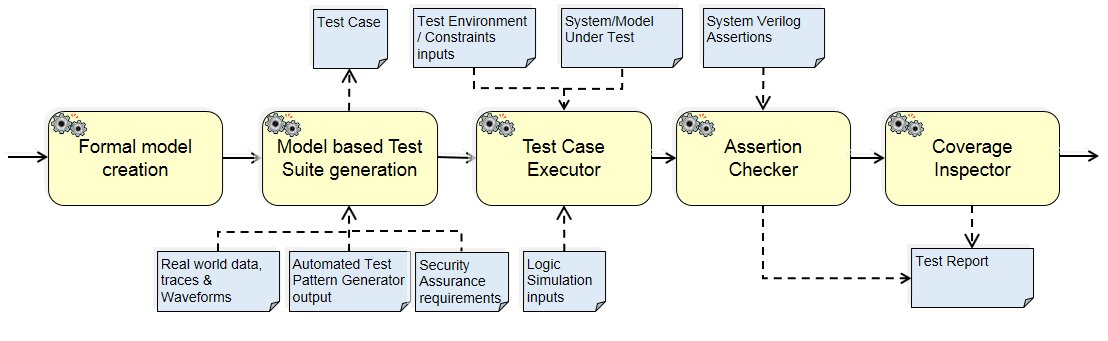
Formal models: Used for V&V of security requirements & functionality before fabrication process.
Certification process: International security evaluation/assessment & standardization committee that qualifies security solutions.
RTL Code: RTL (Register Transfer Level) coding also called Dataflow design step abstracts the given digital design by just describing how the data is transformed as it passes from one register to another. I.e. It is high level abstraction code that describes circuit’s registers, combination function blocks & finite state machines as well as the sequence of transfers between them without describing the actual hardware to carry out these operation. The Synthesis step takes care of translation & optimization of RTL description as per the given HW components.
Netlist: It is the outcome of synthesis step of digital design which is the actual implementation or gate level description of RTL code. It takes standard cell library, constraints & RTL code as inputs and generates a gate level netlist.
Layout: This is then the next step of IC design flow where gate level netlists are converted into physical or geometric representation. Here various logic blocks & their input output pads are placed in the IC area as per the design constraint (floor planning). After this step, detailed routing process is performed to interconnect all the elements.
Security Targets: It is a Common Criteria specification that represents a set of security requirements to be used as the basis of an evaluation of an identified Target of Evaluation (TOE). It defines the boundary, specifies completely & exhaustively the security & functional requirements of the target. It submitted by the device or IC vendor to certification/standardization body for product evaluation process.
Protection Profiles: A protection profile (PP) is the specific set of security features required of a technology to claim compliance with Common Criteria (CC). It is a combination of threats, security objectives, assumptions, security functional requirements (SFRs), security assurance requirements (SARs) and rationales. In order to get a product evaluated and certified according to the CC, the product vendor has to define a Security Target (ST) which may comply with one or more PPs. In this way a PP may serve as a template for the product’s ST.
System Requirements: It is in general all the functional & non-functional requirements of an IC to be designed. It can be requirements related to cost, constraints, operation, regulations, performance, process, platform, quality, reliability, safety, scheduling etc.
Actions/Collaborations
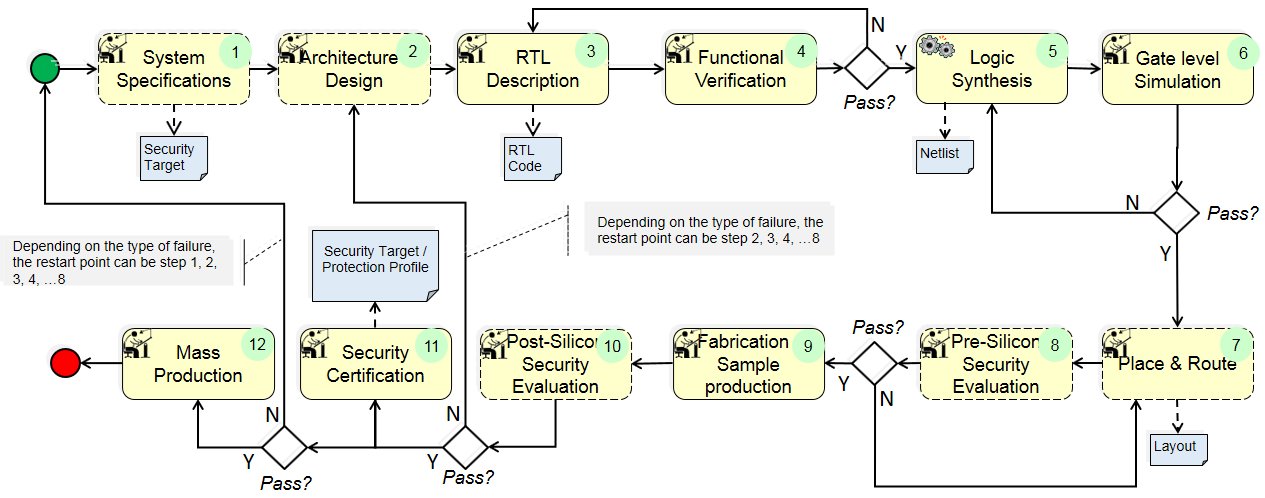
(1) System specifications: define the technical & functional requirements for a security IC.
(2) Architecture design: Transforms system specification into functional HW& SW IP blocks.
(3) RTL Description: Is an abstract modeling of hardware description languages used in digital design that is composed of sequential (registers) and combinational circuit logic description.
(4) Functional verification: High level functionality test block that verifies if system specifications are correctly implemented.
(5) Logic Synthesis: Process step that convert RTL code into synthesizable netlists.
(6) Gate level Simulation: component level functionality test done before IC is sent for manufacturing.
(7) Place & Route: Area, Power, Timing optimization step before fabrication.
(8) Pre-Silicon security evaluation: Test & Verification of IP against security target to ensure that security assurance requirements are satisfied fully.
(9) Fabrication: Realizing the IC on silicon wafer.
(10) Post – Silicon security evaluation: IC validation process against security functional requirements, assumptions & pre-requisites.
(11) Security Certification: Security qualification of the IC against claimed/evaluated assurance levels by standardization committee.
(12) Mass production: Industrialization of IC for commercial & business reason.
Discussion
– The pattern describes a generic process followed in designing an integrated circuit & certification. Real world implementation may vary from the described process. The pattern not only describes the standard IC design flow but also customization needed for certification process.
– The pattern concentrates mostly on digital design to simplify the process.
– Security certification is relevant for applications handling sensitive data like e-Governance, Banking, Access control etc.
– Certification process & requirements vary based on application.
Application Example
ENABLE-S3 UC7 “Touch and Go Assistant (TAGA)”: The pattern is not directly applied in use case, because the use case uses NXP’s security controller that has been designed using process described in the pattern.
The pattern is applicable to smartcard design which finds application in governmental identity services, transport, healthcare, loyalty, banking, whitegoods (smartphones, laptops)
Relations to other Patterns
| Pattern Name | Relation |
| Formalized Analysis and Verification | Formal modelling is a part of IC security certification process |
| MiL (Model in the Loop) | Formal models, fault models etc are used in IC security certification |
| SiL (Software in the Loop) | RTL Description phase of IC security certification process uses RTL code generated from hardware description languages |
| HiL (Hardware in the Loop) | Fabricated ICs are used for HIL V&V process |
| Scenario-based V&V Process | Different attack scenarios are conceptualized and tested during side channel security analysis |
